Checkpoint Integrity Agent Uninstall
Instagram Integrity Checkpoint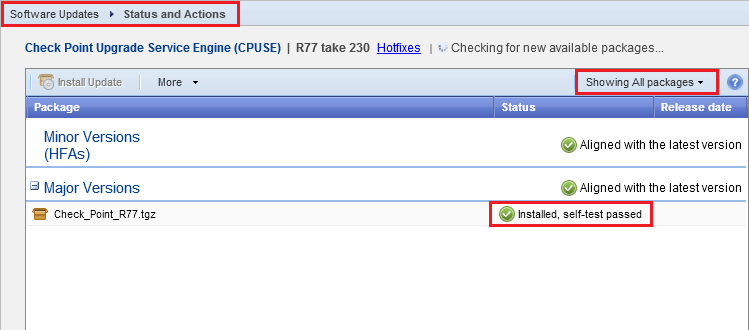 How can I uninstall Check Point Integrity 6 automatically program requires known password to uninstall. Hi All,Been pulling my hair out for the last two days trying to find a way around this. Weve recently decided to give our old client side firewall solution Check Point Integrity 6 the flick, and switch to a different vendor. The problem Im having is trying to come up with a way to automatically remove this software from 5. All machines running Windows XP SP2. Preferably a batch filecommand line solution so I can just throw it in the login script. Check Point Integrity was essentially a corporate version of Zone. Checkpoint Deployment Agent Uninstall
How can I uninstall Check Point Integrity 6 automatically program requires known password to uninstall. Hi All,Been pulling my hair out for the last two days trying to find a way around this. Weve recently decided to give our old client side firewall solution Check Point Integrity 6 the flick, and switch to a different vendor. The problem Im having is trying to come up with a way to automatically remove this software from 5. All machines running Windows XP SP2. Preferably a batch filecommand line solution so I can just throw it in the login script. Check Point Integrity was essentially a corporate version of Zone. Checkpoint Deployment Agent Uninstall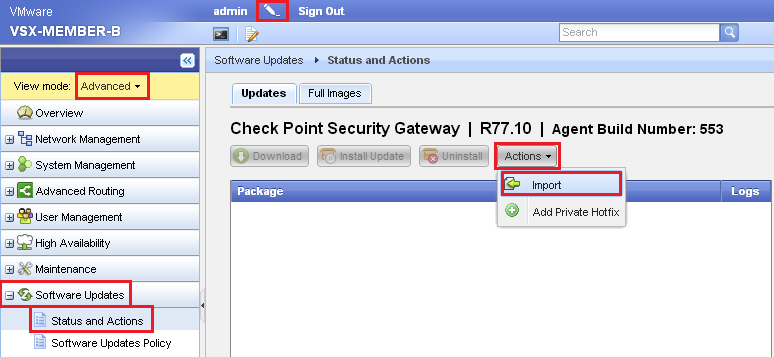 Alarm, and runs the True Vector service underneath everything for the actual firewalling. Manually uninstalling the software is simple enough, the tricky bit is that it asks for an uninstall password to be entered during the removal process and I cant seem to think of a way to automate this. Does anybody have any ideasCustomers can download the ESOD server from http The SSL Network Extender. If the user wishes to uninstall the SSL Network Extender. Check Point endpoint security solutions provides complete coverage including data and network security. With Check Point SandBlast Agent. Cant deploy a cube project to the Analysis Server using BIDS. Checkpoint Integrity Agent. Cheers, Graeme. Edit I have found a way to remove the Integrity component of this package from the command line, but the True Vector service remains in place unless I login through Safe Mode, which is obviously not feasible across multiple client machines. Enter. Password. jpg. SSL Network Extender. Introduction to the SSL Network Extender. Whenever users access the organization from remote locations, it is essential that not only the usual requirements of secure connectivity be met but also the special demands of remote clients. These requirements include Connectivity The remote client must be able to access the organization from various locations, even if behind a NATing device, Proxy or Firewall. The range of applications available must include web applications, mail, file shares, and other more specialized applications required to meet corporate needs. Secure connectivity Guaranteed by the combination of authentication, confidentiality and data integrity for every connection. Usability Installation must be easy. No configuration should be required as a result of network modification. The given solution should be seamless for the connecting user. To resolve these issues, a secure connectivity framework is needed to ensure that remote access to the corporate network is securely enabled. The SSL Secure Socket Layer Network Extender is a simple to implement remote access solution. A thin client is installed on the users machine. The SSL Network Extender client has a much smaller size than other clients. It is connected to an SSL enabled web server that is part of the Enforcement Module. By default, the SSL enabled web server is disabled. It is activated by using the Smart. Dashboard, thus enabling full secure IP connectivity over SSL. The SSL Network Extender requires a server side configuration only, unlike other remote access clients. Once the end user has connected to a server, the thin client is downloaded as an Active. X component, installed, and then used to connect to the corporate network using the SSL protocol. It is much easier to deploy a new version of the SSL Network Extender client than it is to deploy a new version of other conventional clients. Note If the Mobile Access blade is active on a Security Gateway, SSL Network Extender works through Mobile Access and not IPsec VPN. In this case, SSL Network Extender must be configured through the Mobile Access blade. If you already had SSL Network Extender configured on an IPsec VPN Security Gateway and then you enable the Mobile Access blade, you must reconfigure SSL Network Extender for the Mobile Access blade. How the SSL Network Extender Works. The SSL Network Extender solution comprises a thin client installed on the users DesktopLaptop and an SSL enabled web server component, integrated into the Security Gateway. To enable connectivity for clients using the SSL Network Extender a Security Gateway must be configured to support Secu. Remote Secure. Client, in addition to a minor configuration specific to SSL Network Extender. The SSL Network Extender may be installed on the users machine by downloading it from a Security Gateway, R5. HFA1. 0 or higher. Commonly Used Concepts. This section briefly describes commonly used concepts that you will encounter when dealing with the SSL Network Extender. It is strongly recommended that you review the Remote Access VPN section of this bookbefore reading this guide. Remote Access VPNRefers to remote users accessing the network with client software such as Secu. Remote Secure. Client, SSL clients, or third party IPsec clients. The Security Gateway provides a Remote Access Service to the remote clients. Remote Access Community. A Remote Access Community, a Check Point concept, is a type of VPN community created specifically for users that usually work from remote locations, outside of the corporate LAN. Office Mode. Office Mode is a Check Point remote access VPN solution feature. It enables a Security Gateway to assign a remote client an IP address. This IP address is used only internally for secure encapsulated communication with the home network, and therefore is not visible in the public network. The assignment takes place once the user connects and authenticates. The assignment lease is renewed as long as the user is connected. The address may be taken either from a general IP address pool, or from an IP address pool specified per user group, using a configuration file. Visitor Mode. Visitor Mode is a Check Point remote access VPN solution feature. Cuestionario Iso Ts 16949. It enables tunneling of all client to Security Gateway communication through a regular TCP connection on port 4. Visitor mode is designed as a solution for firewalls and Proxy servers that are configured to block IPsec connectivity. Endpoint Security on Demand. Endpoint Security on Demand ESOD may be used to scan endpoint computers for potentially harmful software before allowing them to access the internal application. When end users access the SSL Network Extender for the first time, they are prompted to download an Active. X component that scans the end user machine for Malware. The scan results are presented both to the Security Gateway and to the end user. SSL Network Extender access is granteddenied to the end user based on the compliance options set by the administrator. ESOD Policy per User Group. Since there are many different kinds of threats to your networks security, different users may require different configurations in order to guard against the increasing number and variety of threats. The ability to configure a variety of ESOD policies enables the administrator to customize the software screening process between different user groups. Screened Software Types. ESOD can screen for the Malware software types listed in the following table Software Type. Description. Worms. Programs that replicate over a computer network for the purpose of disrupting network communications or damaging software or data. Trojan horses. Malicious programs that masquerade as harmless applications. Hacker tools. Tools that facilitate a hackers access to a computer andor the extraction of data from that computer. Keystroke loggers. Programs that record user input activity that is, mouse or keyboard use with or without the users consent. Some keystroke loggers transmit the recorded information to third parties. Adware. Programs that display advertisements, or records information about Web use habits and store it or forward it to marketers or advertisers without the users authorization or knowledge. Browser plug ins. Programs that change settings in the users browser or adds functionality to the browser. Some browser plug ins change the default search page to a pay per search site, change the users home page, or transmit the browser history to a third party. Dialers. Programs that change the users dialup connection settings so that instead of connecting to a local Internet Service Provider, the user connects to a different network, usually a toll number or international phone number. Cookies that are used to deliver information about the users Internet activity to marketers. Other undesirable software. Any unsolicited software that secretly performs undesirable actions on a users computer and does not fit any of the above descriptions. Gazzetta Dello Sport Pdf Gratis. Special Considerations for the SSL Network Extender. This section lists SSL Network Extender special considerations, such as pre requisites, features and limitations Pre Requisites. The SSL Network Extender pre requisites are listed below Client side Pre Requisites. The SSL Network Extender client side pre requisites are listed below Remote client must be running the following Windows 2. Pro. Windows XP Home Edition and Pro. Windows Vista. Linux RHEL 3. Linux Suse 9 and up.
Alarm, and runs the True Vector service underneath everything for the actual firewalling. Manually uninstalling the software is simple enough, the tricky bit is that it asks for an uninstall password to be entered during the removal process and I cant seem to think of a way to automate this. Does anybody have any ideasCustomers can download the ESOD server from http The SSL Network Extender. If the user wishes to uninstall the SSL Network Extender. Check Point endpoint security solutions provides complete coverage including data and network security. With Check Point SandBlast Agent. Cant deploy a cube project to the Analysis Server using BIDS. Checkpoint Integrity Agent. Cheers, Graeme. Edit I have found a way to remove the Integrity component of this package from the command line, but the True Vector service remains in place unless I login through Safe Mode, which is obviously not feasible across multiple client machines. Enter. Password. jpg. SSL Network Extender. Introduction to the SSL Network Extender. Whenever users access the organization from remote locations, it is essential that not only the usual requirements of secure connectivity be met but also the special demands of remote clients. These requirements include Connectivity The remote client must be able to access the organization from various locations, even if behind a NATing device, Proxy or Firewall. The range of applications available must include web applications, mail, file shares, and other more specialized applications required to meet corporate needs. Secure connectivity Guaranteed by the combination of authentication, confidentiality and data integrity for every connection. Usability Installation must be easy. No configuration should be required as a result of network modification. The given solution should be seamless for the connecting user. To resolve these issues, a secure connectivity framework is needed to ensure that remote access to the corporate network is securely enabled. The SSL Secure Socket Layer Network Extender is a simple to implement remote access solution. A thin client is installed on the users machine. The SSL Network Extender client has a much smaller size than other clients. It is connected to an SSL enabled web server that is part of the Enforcement Module. By default, the SSL enabled web server is disabled. It is activated by using the Smart. Dashboard, thus enabling full secure IP connectivity over SSL. The SSL Network Extender requires a server side configuration only, unlike other remote access clients. Once the end user has connected to a server, the thin client is downloaded as an Active. X component, installed, and then used to connect to the corporate network using the SSL protocol. It is much easier to deploy a new version of the SSL Network Extender client than it is to deploy a new version of other conventional clients. Note If the Mobile Access blade is active on a Security Gateway, SSL Network Extender works through Mobile Access and not IPsec VPN. In this case, SSL Network Extender must be configured through the Mobile Access blade. If you already had SSL Network Extender configured on an IPsec VPN Security Gateway and then you enable the Mobile Access blade, you must reconfigure SSL Network Extender for the Mobile Access blade. How the SSL Network Extender Works. The SSL Network Extender solution comprises a thin client installed on the users DesktopLaptop and an SSL enabled web server component, integrated into the Security Gateway. To enable connectivity for clients using the SSL Network Extender a Security Gateway must be configured to support Secu. Remote Secure. Client, in addition to a minor configuration specific to SSL Network Extender. The SSL Network Extender may be installed on the users machine by downloading it from a Security Gateway, R5. HFA1. 0 or higher. Commonly Used Concepts. This section briefly describes commonly used concepts that you will encounter when dealing with the SSL Network Extender. It is strongly recommended that you review the Remote Access VPN section of this bookbefore reading this guide. Remote Access VPNRefers to remote users accessing the network with client software such as Secu. Remote Secure. Client, SSL clients, or third party IPsec clients. The Security Gateway provides a Remote Access Service to the remote clients. Remote Access Community. A Remote Access Community, a Check Point concept, is a type of VPN community created specifically for users that usually work from remote locations, outside of the corporate LAN. Office Mode. Office Mode is a Check Point remote access VPN solution feature. It enables a Security Gateway to assign a remote client an IP address. This IP address is used only internally for secure encapsulated communication with the home network, and therefore is not visible in the public network. The assignment takes place once the user connects and authenticates. The assignment lease is renewed as long as the user is connected. The address may be taken either from a general IP address pool, or from an IP address pool specified per user group, using a configuration file. Visitor Mode. Visitor Mode is a Check Point remote access VPN solution feature. Cuestionario Iso Ts 16949. It enables tunneling of all client to Security Gateway communication through a regular TCP connection on port 4. Visitor mode is designed as a solution for firewalls and Proxy servers that are configured to block IPsec connectivity. Endpoint Security on Demand. Endpoint Security on Demand ESOD may be used to scan endpoint computers for potentially harmful software before allowing them to access the internal application. When end users access the SSL Network Extender for the first time, they are prompted to download an Active. X component that scans the end user machine for Malware. The scan results are presented both to the Security Gateway and to the end user. SSL Network Extender access is granteddenied to the end user based on the compliance options set by the administrator. ESOD Policy per User Group. Since there are many different kinds of threats to your networks security, different users may require different configurations in order to guard against the increasing number and variety of threats. The ability to configure a variety of ESOD policies enables the administrator to customize the software screening process between different user groups. Screened Software Types. ESOD can screen for the Malware software types listed in the following table Software Type. Description. Worms. Programs that replicate over a computer network for the purpose of disrupting network communications or damaging software or data. Trojan horses. Malicious programs that masquerade as harmless applications. Hacker tools. Tools that facilitate a hackers access to a computer andor the extraction of data from that computer. Keystroke loggers. Programs that record user input activity that is, mouse or keyboard use with or without the users consent. Some keystroke loggers transmit the recorded information to third parties. Adware. Programs that display advertisements, or records information about Web use habits and store it or forward it to marketers or advertisers without the users authorization or knowledge. Browser plug ins. Programs that change settings in the users browser or adds functionality to the browser. Some browser plug ins change the default search page to a pay per search site, change the users home page, or transmit the browser history to a third party. Dialers. Programs that change the users dialup connection settings so that instead of connecting to a local Internet Service Provider, the user connects to a different network, usually a toll number or international phone number. Cookies that are used to deliver information about the users Internet activity to marketers. Other undesirable software. Any unsolicited software that secretly performs undesirable actions on a users computer and does not fit any of the above descriptions. Gazzetta Dello Sport Pdf Gratis. Special Considerations for the SSL Network Extender. This section lists SSL Network Extender special considerations, such as pre requisites, features and limitations Pre Requisites. The SSL Network Extender pre requisites are listed below Client side Pre Requisites. The SSL Network Extender client side pre requisites are listed below Remote client must be running the following Windows 2. Pro. Windows XP Home Edition and Pro. Windows Vista. Linux RHEL 3. Linux Suse 9 and up.